How to check Azure Key Vault Secret Expiry using Log Analytics Workspace
Requirements
- Azure Key Vault
- Log Analytics Workspace
Solution
First, you need to create Azure Key Vault and Log Analytics Workspace but that is not part of this blog.
I assume you already have those resources created or need to be created.
You need to enable diagnostic settings on our Key Vault and send all logs to our Log Analytics Workspace.
Diagnostic Settings
Navigate to Your Key Vault > Diagnostic Settings > + Add Diagnostic Setting.
Select all category groups and metrics, then select Send to Log Analytics workspace and choose your destination Log Analytics Workspace:
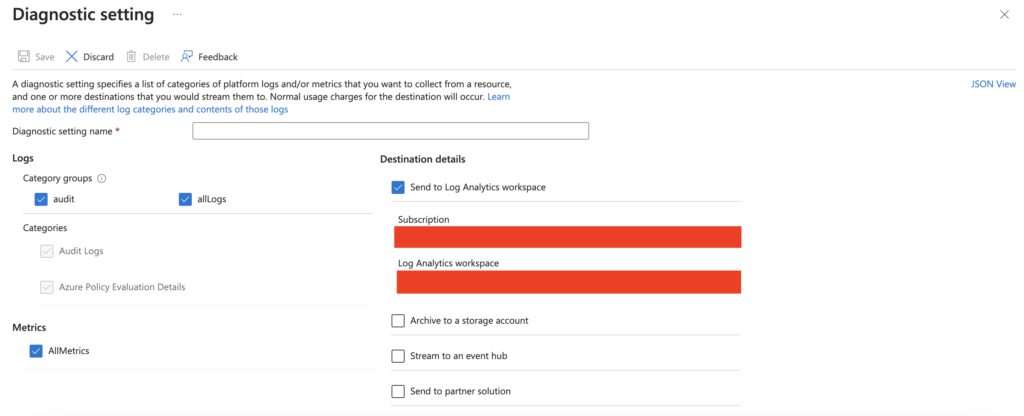
After you have enabled diagnostic settings, save the settings.
Now go to Monitor > Logs.
Select the scope you want to run the query for.
You need to add a simple query to check if any Key Vault is expired or near expiry.
let lastIndexof = (input:string, lookup: string) {
strlen(input) - indexof(reverse(input), reverse(lookup)) - strlen(lookup)
};
AzureDiagnostics
| where OperationName contains "SecretNearExpiry" or OperationName contains "SecretExpired"
| extend KeyVaultName = column_ifexists('eventGridEventProperties_data_VaultName_s', 'N/A')
| extend KeyVaultType = column_ifexists('eventGridEventProperties_data_ObjectType_s', 'N/A')
| extend Name = column_ifexists('eventGridEventProperties_data_ObjectName_s', 'N/A')
| extend EventType = column_ifexists('eventGridEventProperties_eventType_s', 'N/A')
| extend EventType = substring(EventType, (lastIndexof(EventType, '.') + 1))
| extend Expiry = column_ifexists('eventGridEventProperties_data_EXP_d', 0)
| extend Expiry = format_datetime(unixtime_seconds_todatetime(Expiry), 'yyyy/MM/dd HH:mm:ss')
| where Name != '' or EventType != ''
| where TimeGenerated > datetime_add('year', -10, now())
| project KeyVaultName, KeyVaultType, Name, EventType, Expiry
| order by Expiry Now save this query to Queries. You can pin this query to your Dashboard also.
